How to create an Amazon S3 bucket Access Policy
In this article we will see how to create an Access Policy that will allow us to limit access to this AWS S3 Bucket to only one user and in the same time limit a user to have access to only one AWS S3 bucket.
Many times you will need to separate user access over AWS objects and you need to make sure they don't have access to each other resources unless you want them to.What is an AWS IAM Policy ?
A policy is a document that formally assigns permissions to a user, group, role, or resource, you create a policy, which is a document that explicitly lists permissions. A policy lets you specify the following: Actions - what action are allowed. Resources - on what resources are the action allowed. Effect - type of the effect on the action. (to enable it or to disable it) What is the format of a policy ? Policies are created using JSON format files and it can have one or more statements, each of which describes one set of permissions. Policy example{
"Version": "2012-10-17",
"Statement": {
"Effect": "Allow",
"Action": "s3:ListBucket",
"Resource": "arn:aws:s3:::my_bucket"
}
}- this policy will allow to list a bucket called my_bucket.
User Access Policy over a single AWS S3 bucket
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": [
"s3:GetBucketLocation",
"s3:ListAllMyBuckets"
],
"Resource": "arn:aws:s3:::*"
},
{
"Effect": "Allow",
"Action": "s3:*",
"Resource": [
"arn:aws:s3:::usrftpjoe-bkt",
"arn:aws:s3:::usrftpjoe-bkt/*"
]
}
]
}How to use Amazon Console to create the policy
1 - Login into you Amazon Console and go to IAM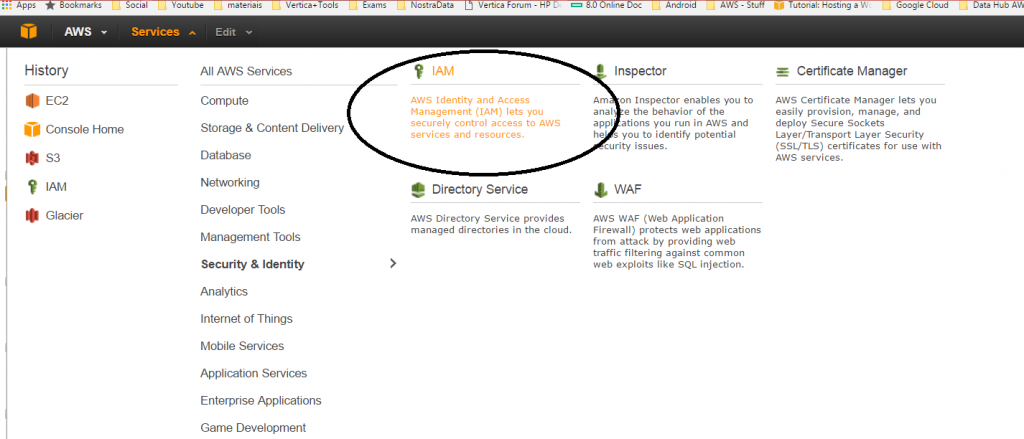 2 - Choose to create a new policy
2 - Choose to create a new policy
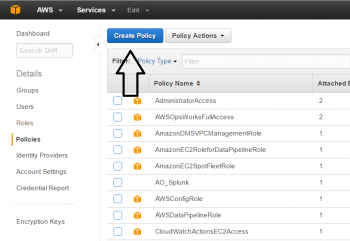 3 - Choose Create Your Own Policy option
3 - Choose Create Your Own Policy option
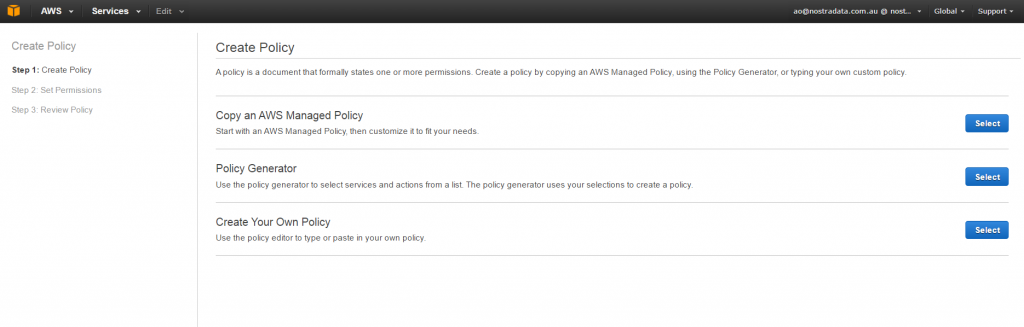 4 - Provide the Name, description and the body the policy. Validate first and then Create the policy.
4 - Provide the Name, description and the body the policy. Validate first and then Create the policy.
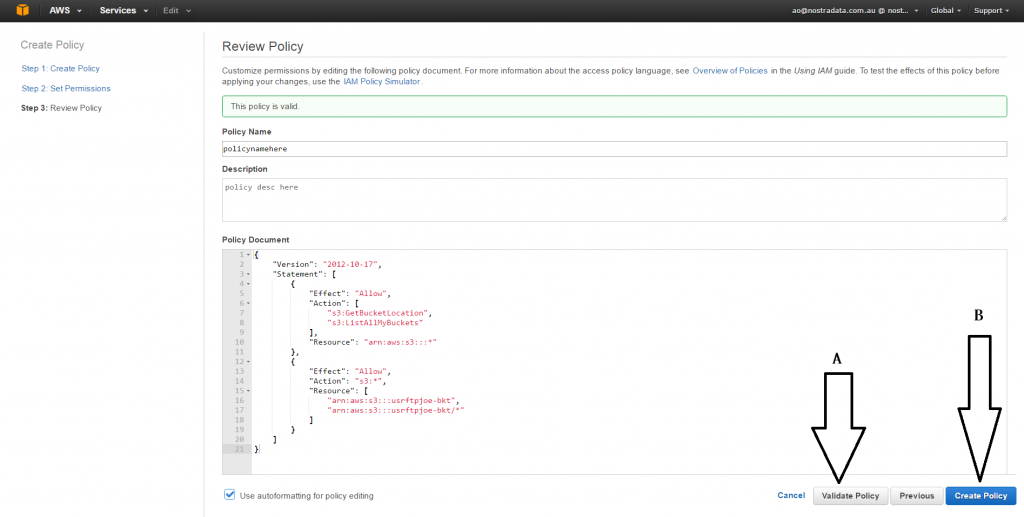
How to use Amazon command line utility to create the policy
aws iam put-user-policy --user-name usrFtpJoe --policy-name usrFtpJoe-S3-access-policy --policy-document /tmp/usrFtpJoe-bucket-policy.jsonYou can attach the policy to a user using the Gui or the command line AWS client.
Use Amazon Console to attach the policy:
1 - Select the policy and Choose Attach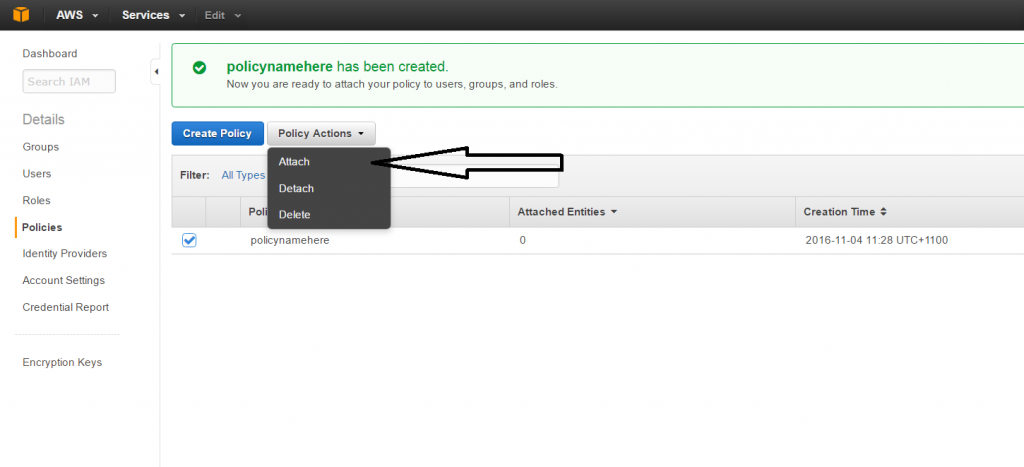 2 - Choose the user to attach the policy to and click on the Attach Policy button.
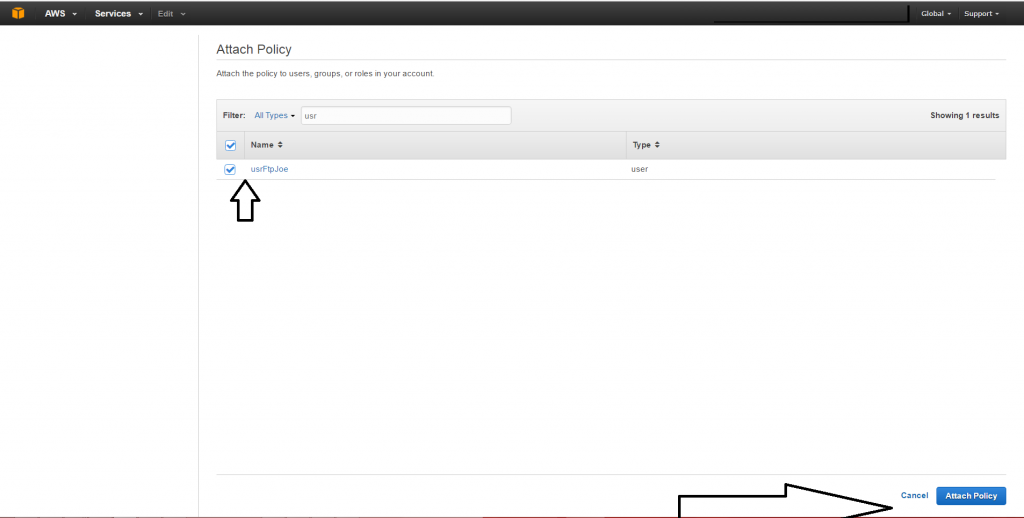
2 - Choose the user to attach the policy to and click on the Attach Policy button.
Use Amazon Command Line utility to attach the policy to a user
aws iam attach-user-policy --policy-arn arn:aws:iam::393556751081:policy/usrFtpJoe-S3-access-policy --user-name usrFtpJoeaws iam list-policies --output text | grep <policy name